*Disclaimer*
Please note, this article has been made to highlight security issues on common and widely used devices and shows an example of how one small flaw can cause a ripple effect which can then cause a greater security risk.
All content below has been gained from Shodan which is publicly searchable and available to any user, all screenshots are examples which are again publicly accessible and are not related to each other but are used to highlight a security risk.
It should also be noted that while using Shodan is perfectly legal, trying to gain access to other systems without strict permission is not.
There are many large search engines such as Google and Bing but theres one small site that may go unnoticed that indexes something a little different.
Shodan crawls the internet for banners or meta data sent from servers to a client before connecting. Searching for Webcam brings up 14945 results in an array of different countries:
The results show a small amount of information but the most interesting parts are the IP Address not shown and the Server – SQ-WEBCAM. Sometimes the camera brand is displayed which helps in tracking down which device the IP links to.
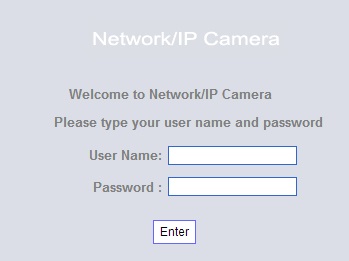
If the IP address is now entered into a browser and works a log-in prompt will appear, this can also display the camera brand or a unique log-in page which can be tracked down on Google. This brand can be searched and the default password found, if the brand is hard to come by entering defaults such as password, admin or root can be done by trail and error.
If this cameras default password has not been changed then the log-in will be successful and full access to the camera will be granted.
Some IP Cameras can be moved remotely and so a logged-in user can scan the environment the camera is currently in, be it someones back garden, garage or even bedroom.
One overlooked feature of these camera is that some are wireless so if a unauthorised user with full access checks the webcam settings the WiFi AP name can be found which on its own is not very useful, but these cameras sometimes store the WiFi passwords in plain text and so with this the victims network is now compromised.
With a little IP location help from Google and checking the cameras surroundings the location of the camera can be narrowed down and is successful an attacker could now arrive at the victims location, log-in to the WiFi with the password pulled from the webcam and now start to attack other computers on the network, spoof traffic or launch other attacks.
An IP Camera installed as a security device to protect a home or business is a good idea but if its own security is not checked this helpful device can soon be used against its user and expose other areas, all from not changing the default password.